How safe are credentials in script packages?
- Details
- Written by Alexander Riedel
- Last Updated: 19 April 2016
- Created: 30 April 2012
- Hits: 14133
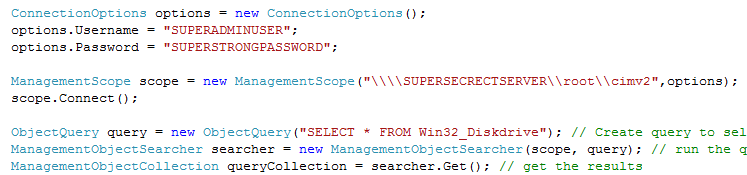
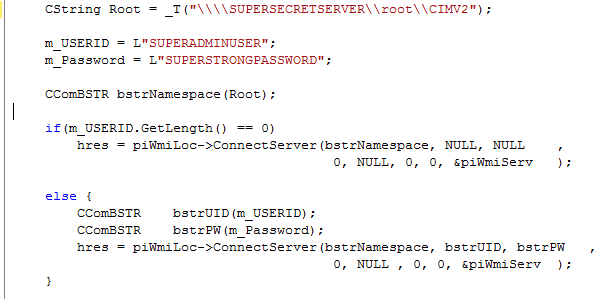
We get that question all the time. Before we start, please note that we do not advise to ever put credentials as plain text into any kind of code. Use encrypted strings, store encrypted credentials in files or, if all else fails, prompt. Now, having said that we all know that sometimes schedules and pressure from “above” forces you to do things you normally wouldn’t do. So for the sake of argument we have created a variety of executables which use SUPERADMINUSER and SUPERSTRONGPASSWORD to run a WMI query on SUPERSECRETSERVER.
We used
- VBScript
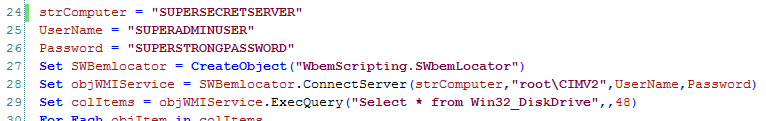
- PowerShell

- C#
- C++
Obviously all of these won’t run in your environment unless you create a server with that name and add those credentials.
If you want to examine the resulting executable files yourself, download WMIQueryExecutables.zip here.
Now we take all these files and open them in PrimalScript as binary files and look for the user id and password, starting with the C++ version.
And here is your password, easily visible in the binary data:
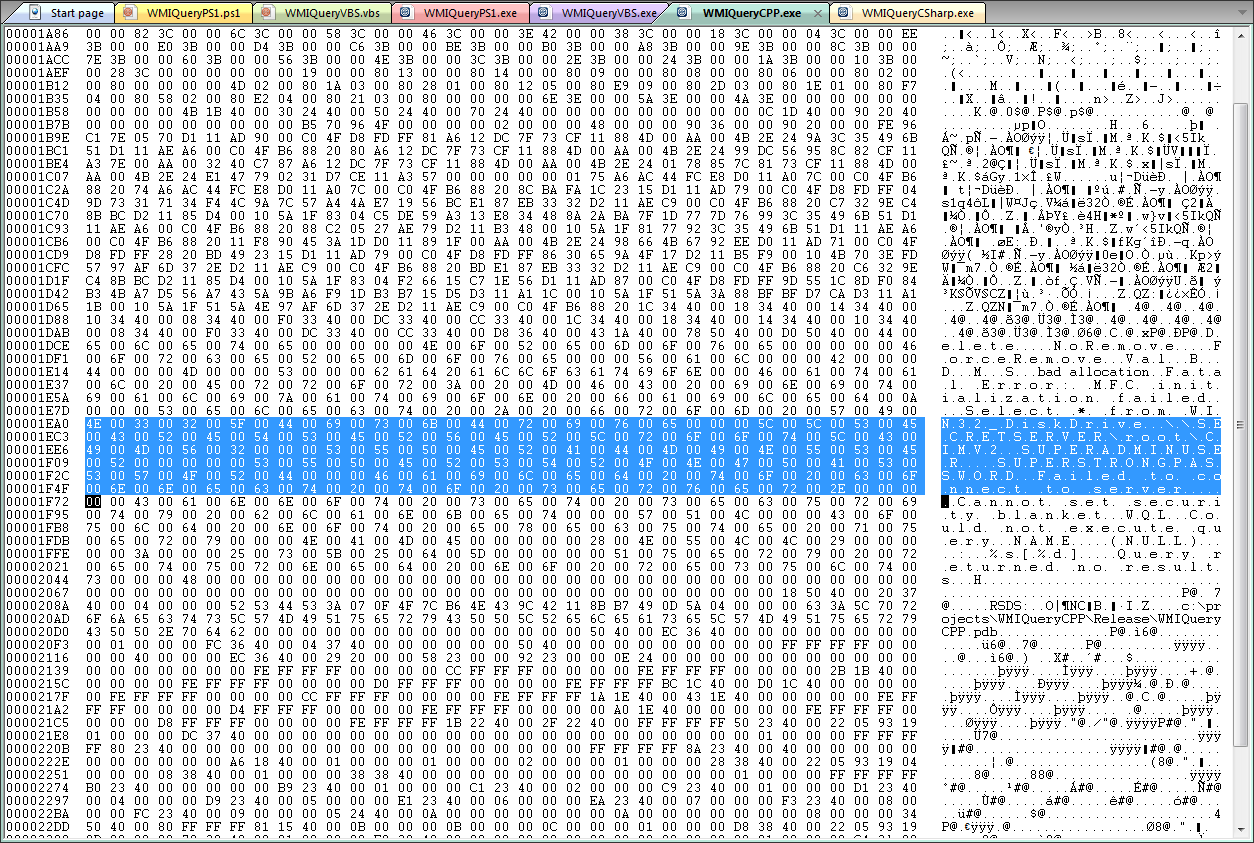
The spacing with NULL characters comes from the string being stored as unicode, so lets search for that in the C# version:
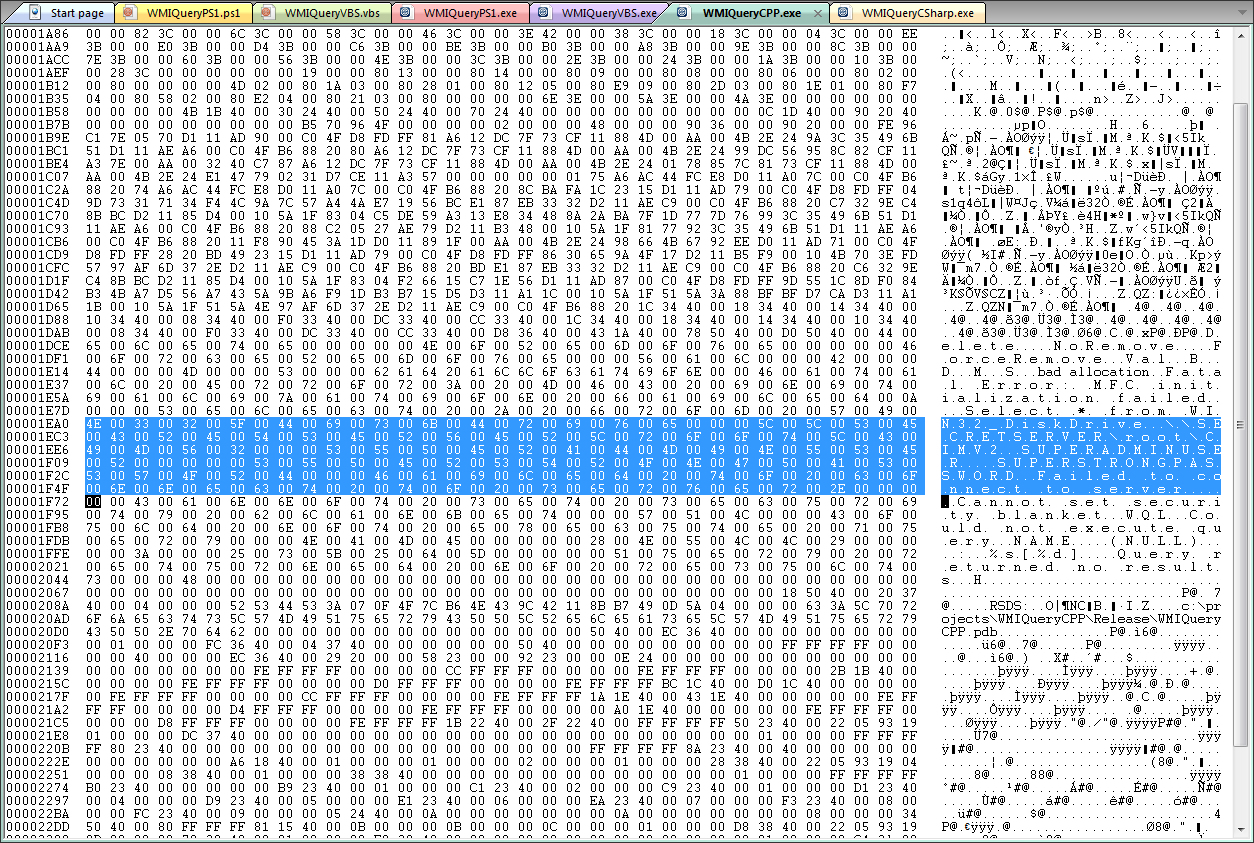
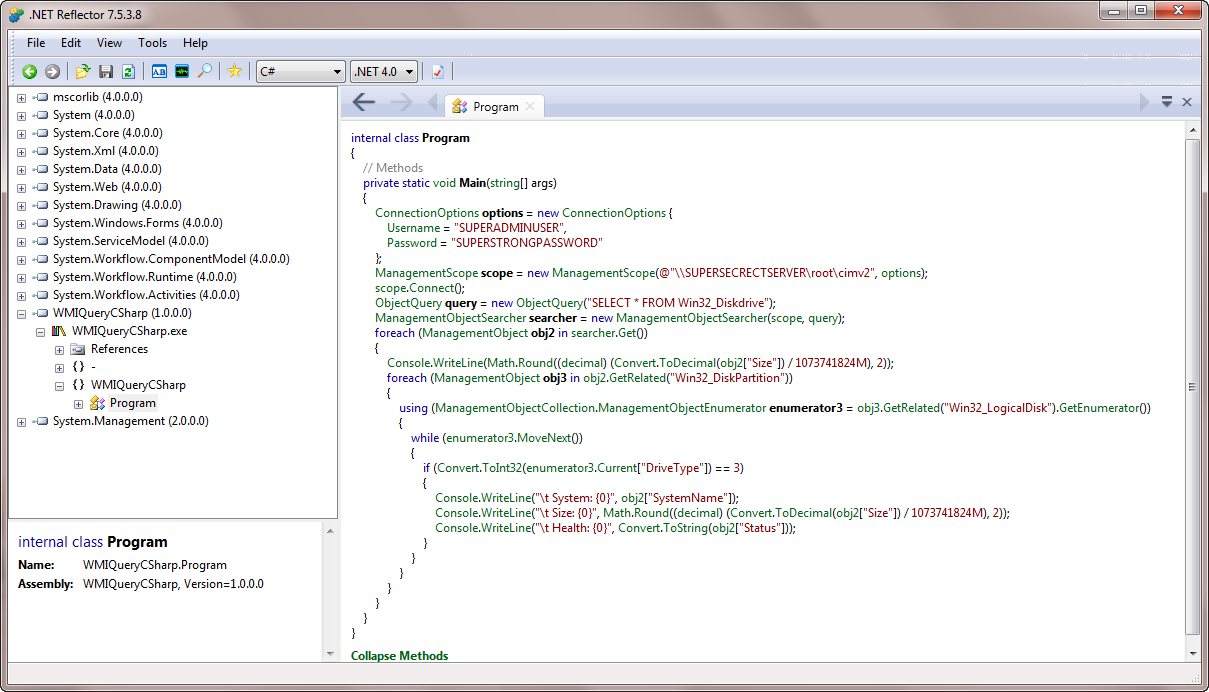
As you can see, we didn’t have to look far. To make matters worse, if you take a disassembly tool to a .NET exe you don’t even have to read binary data:
Now let’s try the script packages created by PrimalScript:
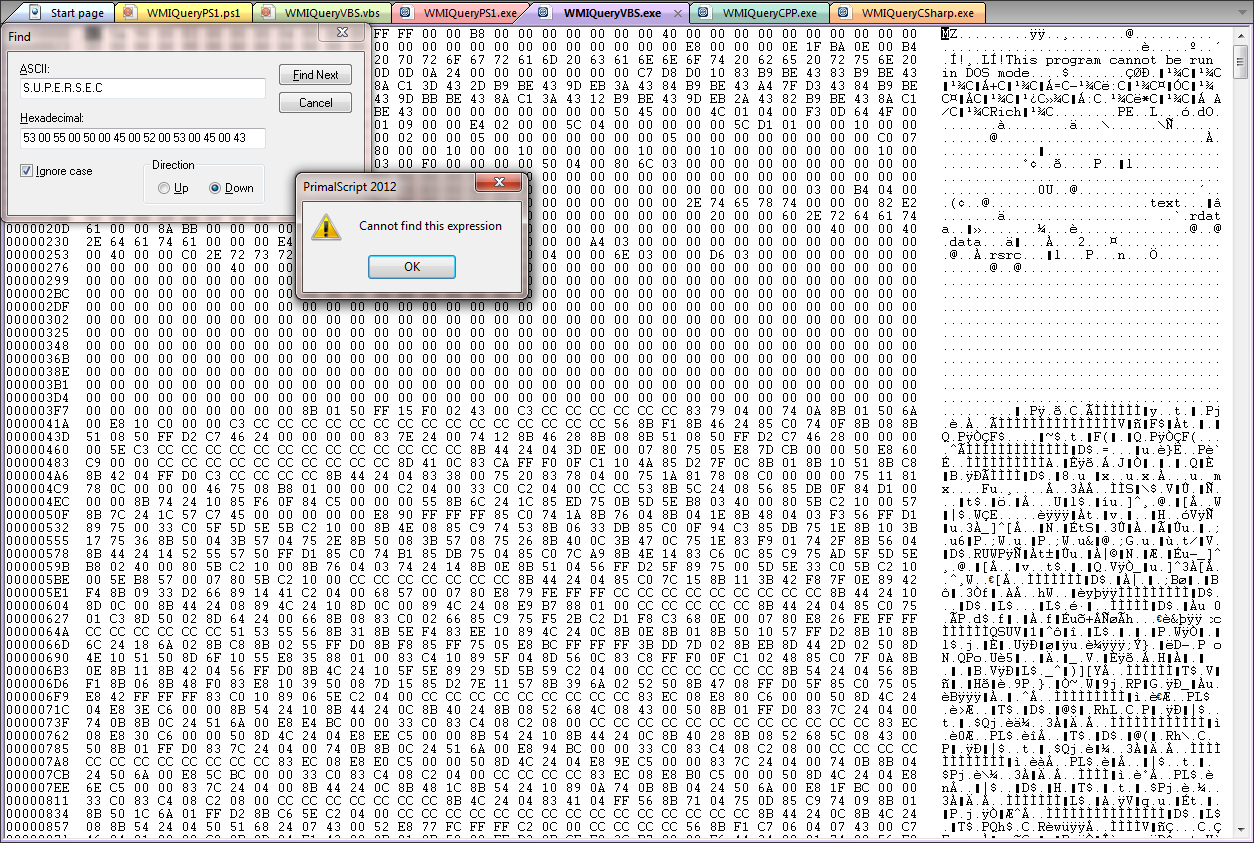
and
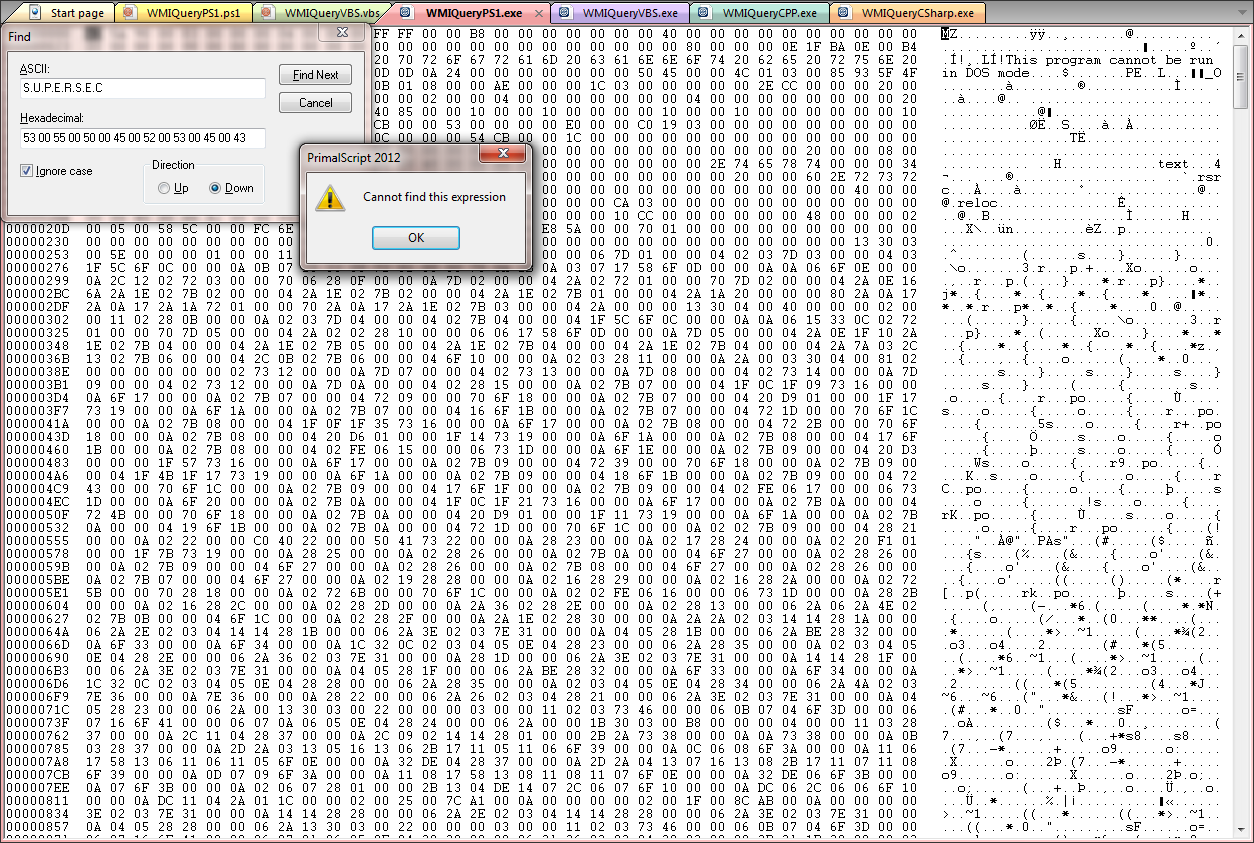
So you see, if you have to, absolutely have to put credentials somewhere, a packaged script is the way to go.
Go ahead, get the binaries and see for yourself.
For licensed customers, use the forum associated with your product in our Product Support Forums for Registered Customers.
For users of trial versions, please post in our Former and Future Customers - Questions forum.

