Enable WMI Explorer Windows 8 Remote Connection Permissions
- Details
- Written by Devin Leaman
- Last Updated: 19 April 2016
- Created: 14 December 2015
- Hits: 13072
Earlier in October of 2015, I wrote an article about remote connection failures that occur when using WMI Explorer on a remote computer running Windows 8. This solution doesn’t apply to computers running other versions of Windows.
To sum it up, you need to make three changes for WMI Explorer to connect to a Windows 8 remote machine.
- Allow Remote Administration through the Windows Firewall
- Give the user the required remote access to COM security
- Give the user the required remote access to the WMI root namespace and sub-namespaces.
For those who have this issue, but don’t have the time to go through all of the steps, I have created a script to solve the problem.
To use the script, run it locally on the remote machine in an elevated session (Run as administrator). This script is not designed to be run remotely, for example, by using Invoke-Command. Because it grants permission to the current user, be sure that the script runs in the user account of the person running WMI Explorer.
To follow the progress of the script, use its Verbose parameter.
About the Script
After digging around for a PowerShell replacement to netsh firewall, I found which seemed like what I needed, but there was just one problem. When running the actual command:
Set-NetFirewallRule –DisplayGroup 'Remote Administration' |
It threw an ObjectNotFound exception, saying that there were no rules with a DisplayGroup equal to ‘Remote Administration’.
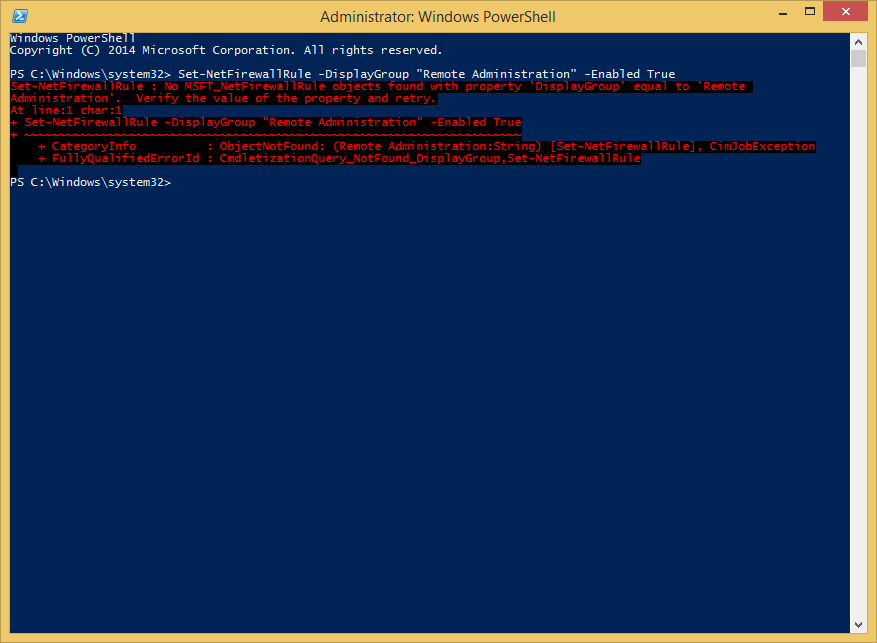
Come to find out that the firewall rules don’t exist until you run:
netsh firewall set service RemoteAdmin enable
|
With that, I decided that, in my script, I would use netsh firewall as opposed to Set-NetFirewallRule to avoid having to build each rule individually and ensure they were configured properly.
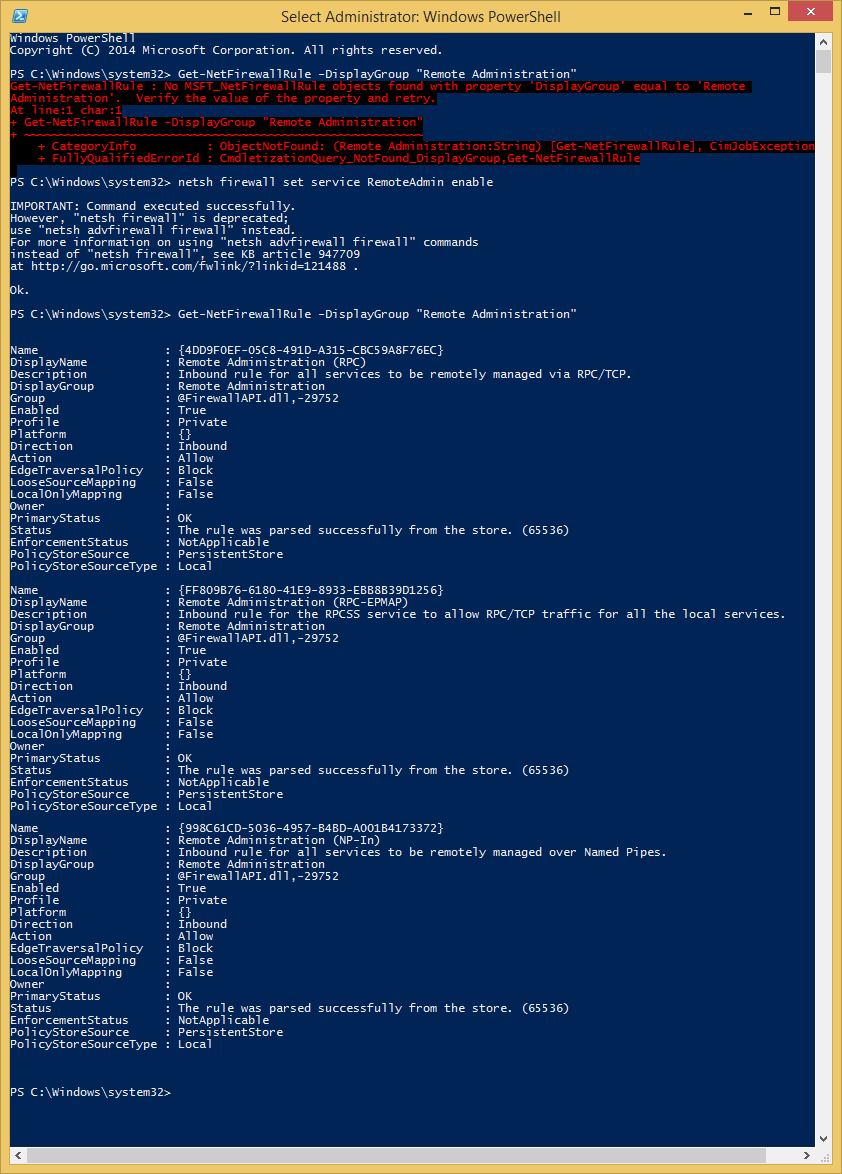
Up next is the COM security permissions. You need to ensure that the current user has remote access permissions. In my original post, I made sure that Everyone had remote access, because it worked and security wasn’t an issue on a VM.
Instead, I asked around and learned that I could assign the current user to the Distributed COM Users group which has remote access permissions by default. To add a user to a group, I found a post by the Scripting Guys describing just how to do this in PowerShell. The big difference between their post and my script was adding $User and $Computer variables to represent the current username and computer name.
The final step was to assign Remote Access rights to the Authenticated Users group so that they can access the root namespace and sub-namespaces. When it comes to doing this in a script, I owe a lot to Karl Mitschke and his post, Script remote DCOM / WMI access for a non admin.
Of course, there were quite a few things that needed to be removed, since we simply don’t need them, such as the $computers variable, foreach loop, and variables associated with DCOM permissions. In his script, the $SDDL variable determines which permissions are set and it is currently set up to give remote access to the specified namespace, but not to the sub-namespaces. By adding CI; to the string, it becomes $SDDL = “A;CI;CCWP;;;$SID” and now it gives the permissions across sub-namespaces as well.
Run the script with Administrator permissions. Download it here: Set-WMIExplorerPermissions_FINAL
For licensed customers, use the forum associated with your product in our Product Support Forums for Registered Customers.
For users of trial versions, please post in our Former and Future Customers - Questions forum.

